Active Directory for your IAM
At Tranquil IT, we are Samba Active Directory experts and systematically advise our clients on the implementation of an AD. Why is Active Directory your ally in everyday life? We will try to explain it to you.
Managing the authentication of its users on its network is nowadays at the heart of concerns, particularly in terms of cybersecurity. You store sensitive data on your network, and you don’t want anyone to be able to access it. It is therefore crucial to set up Identity and Access Management (IAM) on your fleet. To do this, you must first make an inventory of your resources for understanding your information system as a whole. Once you know your resources, you need to define who has access to which on your network. In short, you need to define your IAM. To set up your IAM, you will need secure and reliable tools. We help you today to better understand what these tools are, and their advantages and disadvantages.
Active Directory: a complete solution
General
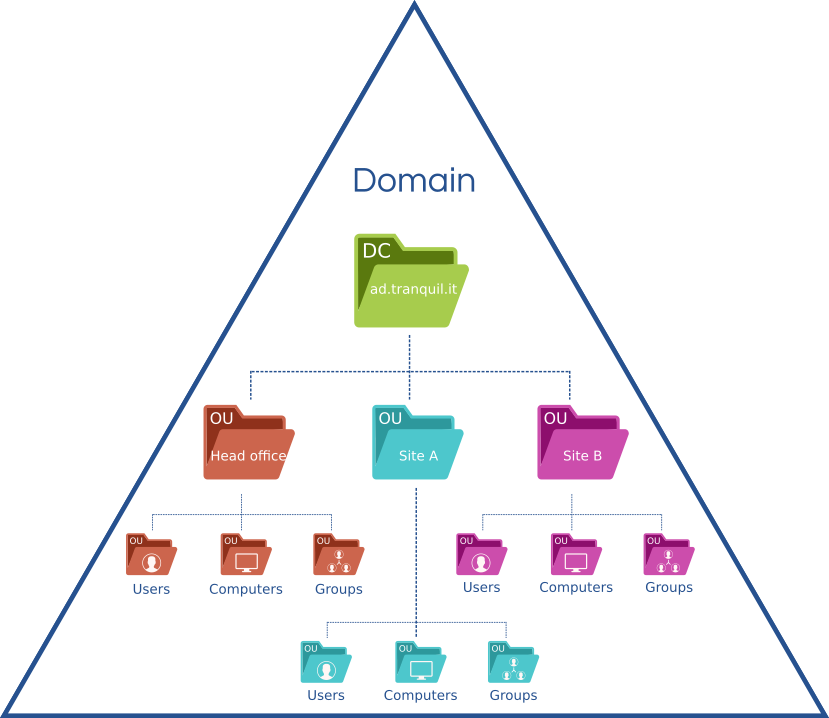
Active Directory is a set of interconnected tools to centralize, manage, and authenticate users and computers of a domain. With Active Directory, you can organize your infrastructure into a main domain segmented into Organizational Units (OU) that group objects (users, printers etc…). This organization allows you to apply a global security policy on your entire fleet, while applying finer strategies on your OU.
By doing a little more research on the subject, you will certainly find that Microsoft Active Directory also allows you to create several hierarchical domains, with approval relationships between each of them. Caution, this practice is not recommended. Approval relationships will complicate the management of your infrastructure and especially the auditability of your informations system.
Active Directory is the heart of your computer network. It lists workstations, servers, users, printers, etc. Active Directory also allows you to apply your security policies to your fleet using GPOs (Group Policy Objects).
Active Directory is based on the protocol Kerberos, which allows you to have secured connections. Kerberos is based on a system of authentication keys and tickets, thus allowing the security of the authentication on your fleet. By authenticating, the client will obtain a temporary connection ticket, allowing him to access other services (e.g. file server, proxy server, business application, etc.) without entering his login and password again.
Our Expert Advice
Active Directory is a powerful set of tools that allows you to properly manage your users’ rights. At Microsoft, this technology is expensive because you have to buy CALs (Client Access Licenses) to use the Active Directory service. We strongly recommend that you use Samba-AD, which is the Open Source alternative to Microsoft Active Directory. The use of Samba Active Directory is free of charge, and management is done via Windows RSAT in the MMC console to facilitate the administration of your network. Thus, Samba offers only advantages.
Tranquil IT is recognized as a Samba Active Directory expert in Europe and we have executed more than 270 audit, skills transfer, migration, and domain merger projects. Our experience of more than 12 years allows us to know the majority of migration scenarios.
There are also alternative solutions to Active Directory to manage the identification and authentication of your users on your fleet. You may have already considered using the following solutions, but we do not recommend using them based on our experiences and knowledge. Here is what we have learned from these experience as sysadmins.
The Workgroup: simple but not scalable
General
A workgroup is a set of workstations under Windows belonging to the same group. The workgroup does not require a server to manage the workstations since the configuration is done on each workstation independently. Thus, you will have to go to each computer in your fleet to configure it. The same applies to the management of users for whom you will have to create an account on each computer that they are likely to use. This mode of operation is convenient for very small organizations, as it does not require centralization of information on a dedicated server. No specific skills are required to set up a workgroup within a company, so if your company is composed of only two computers , you can run them in a workgroup. Beyond two positions, the workgroup is to be avoided. You will quickly be overwhelmed by the growing number of workstations, and your network will not be secure.
Our expert advice
We do not recommend a workgroup organization because it provides very few benefits in relation to the obstacles to be overcome. The workgroup is a temporary organization that will be useful for the creation of your company, but you will quickly need to replace it with a more appropriate solution such as Active Directory. Too often we see system administrators overwhelmed by the management of their infrastructure because of the workgroup. Conclusion: do not choose the workgroup, whatever your reasons.
- A simple infrastructure
- No need for a centralized server
- Expensive to set up
- No flexibility on the number of workstations
- No centralization of information
- Not secure
The NT4 domain: already obsolete
General
The NT 4 domain is limited to the directory role. Your domain will therefore group together only the identification and authentication information of your users, as well as the machines authorized to access the network.
At each connection, the user will enter their login and password on an A machine. This action will launch a request to the Domain controller which will check if the couple user + password has the right to connect to the machine A.
The NT 4 domain has no memory concerning user authentication. Indeed, the Kerberos protocol is only implemented in Active Directory. Thus, each time the user wants to connect to a network service, they will have to enter their login/password again.
The NT 4 domain has been at the heart of concerns recently. Indeed, the new versions of Windows 10 (1803 and above) no longer fit into an NT 4 domain. Since then, a patch has been announced by Microsoft and these versions of Windows can be integrated into an NT 4 domain again, which still represents a first alert regarding NT 4 domain support. These domains are now obsolete, and even if Microsoft continues to maintain them, we can imagine that this will no longer be the case very soon, especially since Microsoft is now turning to the Cloud with Azure.
Our expert advice
Implementing an NT 4 domain today is inconceivable because there is a newer and less expensive technology than Active Directory.
If you are already under NT 4 domain, we advise you to quickly learn about Active Directory to prevent the end of NT 4 support. NT 4 is an obsolete technology and limited in terms of functionality. A migration is to be considered, either to a Microsoft Active Directory or to Samba Active Directory, the Open Source alternative.
- N/A
- Obsolete organization that is no longer maintained since 2000 by Microsoft and since 2017 at Samba
End of CentOS 7 support
With the end of CentOS 7 support, WAPT software users need to consider alternatives to continue benefiting from updates and new features. WAPT version 2.6 requires a still-supported Linux distribution, which excludes CentOS 7. Here is an overview of the options...
Stakes and migration: the impact of the end of Windows 10
Microsoft has officially announced the end of support for Windows 10 as of October 14, 2025. In concrete terms, this means that hundreds of millions of users will have to consider a transition to a new operating system, in particular Windows 11. One of the main issues...
Discover PeerCache functionality with WAPT
Downloading large files, especially in corporate environments, can quickly saturate bandwidth. That's where PeerCache, comes in.mORMot GET (mget) and the PeercacheThis is an open-source command-line program, similar to the wget tool, that allows you to download files...