WAPT : Discovery of a security breach
Recently, we were contacted by an organization informing us about the discovery of a significant security vulnerability related to WAPT. Find all the important details in this article, including the fix for the vulnerability.
The security breach in WAPT
During a Red Team mission, the ITT&AC (Independent Technical & Automation Center) team at BNP Paribas discovered a security vulnerability. This vulnerability, identified by “Anass Annour from the Risk ORM/ITT&AC team at BNP Paribas,” was previously unknown (Zero Day).
This vulnerability allows users to elevate their privileges via the WAPT agent. For obvious security reasons, we cannot disclose more details about the nature or operation of this flaw.
We want to emphasize that this vulnerability is significant and needs to be addressed promptly. You can refer to the CVSS score of this vulnerability for more information.
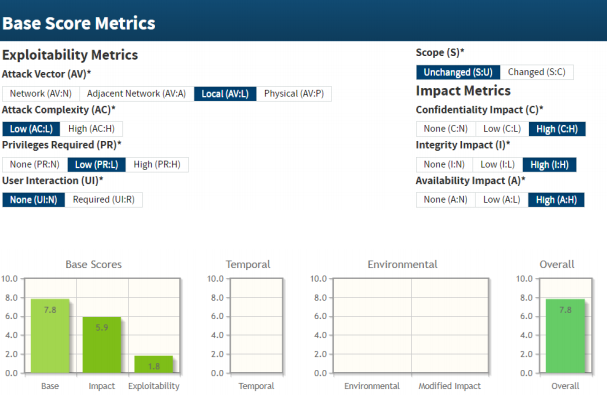
In the field of cybersecurity, the CVSS score allows the standardized evaluation, based on objective and measurable criteria, of the criticality of a vulnerability. CVSS stands for Common Vulnerability Scoring System. This assessment is based on three precise metrics:
- The Base Metric.
- The Temporal Metric.
- The Environmental Metric.
What is a Red Team?
A Red Team is a team whose objective is to test the cybersecurity of your systems by attempting to hack them. Its members simulate malicious attacks aimed at penetrating the systems they are tasked to study. These actions are carried out in a benevolent and preventive manner, aiming to identify vulnerabilities so that they can be addressed as quickly as possible. Red Teams are often contrasted with Blue Teams or even Purple Teams, each having different objectives and operational methods.
Quickly fix the security breach
We are now able to provide a patch to address this security vulnerability. Therefore, we can communicate about it in accordance with the “responsible disclosure” process.
The patch is straightforward to implement as you simply need to update WAPT. Two versions are available to facilitate this process:
- Choose WAPT 2.0.0.9450: Hash 7bc6920c
- Choose WAPT 1.8.2.7373: Hash e96e569c
Since the security flaw involves privilege escalation, you can use the “TIS-AUDIT-LOCAL-ADMINS” package (available for free on the WAPT Store) to verify everything is in order across your IT infrastructure. Additionally, these links will be useful if you want to learn more about this security issue:
What is Responsible Disclosure?
Responsible Disclosure is a model for disclosing computer vulnerabilities. This method, based on full disclosure principles, aims to publish vulnerabilities as early as possible. However, Responsible Disclosure also seeks to allow sufficient time for the affected organization to provide a fix before the vulnerability is publicly disclosed.
What is a CVE?
CVE, or Common Vulnerabilities and Exposures, refers to a public and international list of computer security vulnerabilities. This initiative is managed by MITRE and supported by the U.S. Department of Homeland Security.
One of the objectives and advantages of WAPT has always been to promote the updating of your software. This helps protect against the risks posed by security vulnerabilities. Unfortunately, this time, this awareness effort goes further as WAPT itself serves as an example. It’s proof that one can never be too cautious and that cybersecurity is an ongoing effort.
End of CentOS 7 support
With the end of CentOS 7 support, WAPT software users need to consider alternatives to...
Stakes and migration: the impact of the end of Windows 10
Microsoft has officially announced the end of support for Windows 10 as of October 14,...
Discover PeerCache functionality with WAPT
Downloading large files, especially in corporate environments, can quickly saturate...